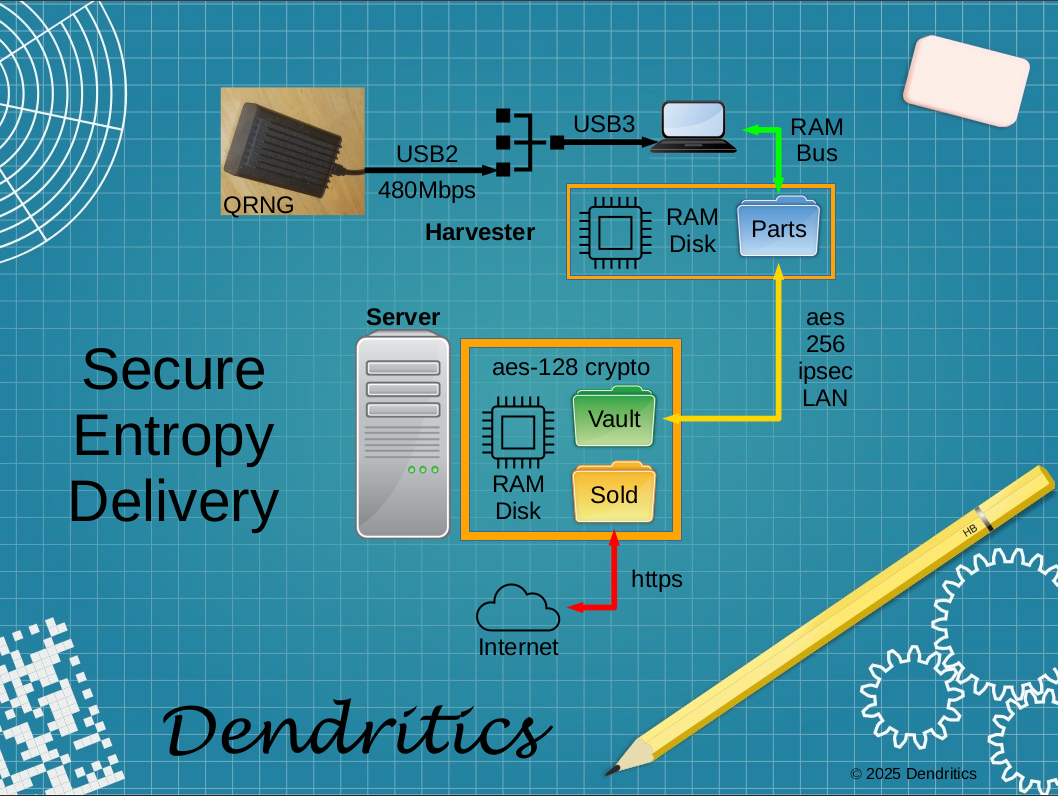
In the age of double and triple-digit gigabyte quantities of system memory, swapping memory to disk is not only cumbersome, but often unnecessary. Linux, our operating system of choice, makes very efficient use main memory, including thinly allocated ram disks on a per-user basis. Their use enhances security by preventing transient images.
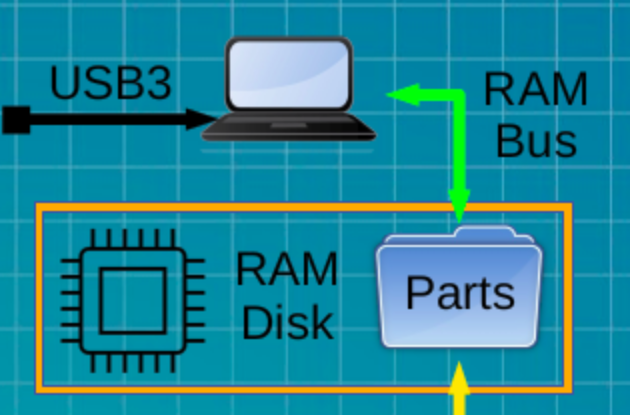
USB devices, in general, are fully accessible to user space on a Linux system. Sequestering access to the Quantum Random Number Generator (QRNG) requires a secure satellite system. The Harvester runs a background process that fills only back-stock parts files on the user ram disk. They move forward only when filled and needed. An NFS export, via secure IP transport, permits a background process on the server to consume forward-stock Parts to assemble back-stock files in the Vault on the Server Ram Disk, and moves them forward in the Vault when ready for sale.
Both Harvester and Server stocking processes rely on the move (mv) command to move completed back-stock files forward. Sale security leverages fact that mv does not copy the file when the move destination resides on the same file-system as the source. In this case, only directory entries are created and removed, leaving the original file in place. This is true for moves from the Vault folder to the Sold folder on the Server Ram Disk.
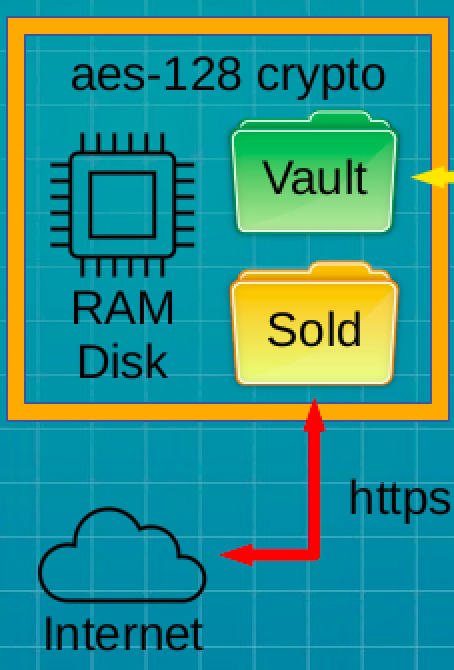
Upon payment approval, the purchaser is presented with the Thank You page, and has one hour to use the Browser Download link. The original WordPress Express Checkout plug-in was modified to support dynamic downloads when specific static files are purchased. The first use of the Browser Download link targets the static text matching your purchase agreement. This action triggers allocation and secure presentation of your unique entropy file.
After refreshing the browser window, a unique and secure download link is presented under Copy Direct URL. Use a right-click and select “Copy link address” to place the long string on your clipboard. This link has unlimited uses for 60 minutes, once created by activating Browser Download. After 60 minutes the file and access structure are purged. Once the Copy Direct URL link may appear, the Browser Download link redirects to the purchased file, and is valid for the remainder of the 60 minute activation window.
A check is performed by the Thank You page to conditionally display the Copy Direct URL link. Once captured, and perhaps transferred to a needy client, the provided https:// Direct URL will dutifully encrypt everything from the 3rd forward-slash to the end of line. This shields your custom download link from prying eyes. 60 minutes after creation, the custom URL will result in a 404 error if used, and the Copy Direct URL will disappear from a refreshed Thank You page.
Questions, suggestions, and comments are invited.
Leave a Reply
You must be logged in to post a comment.