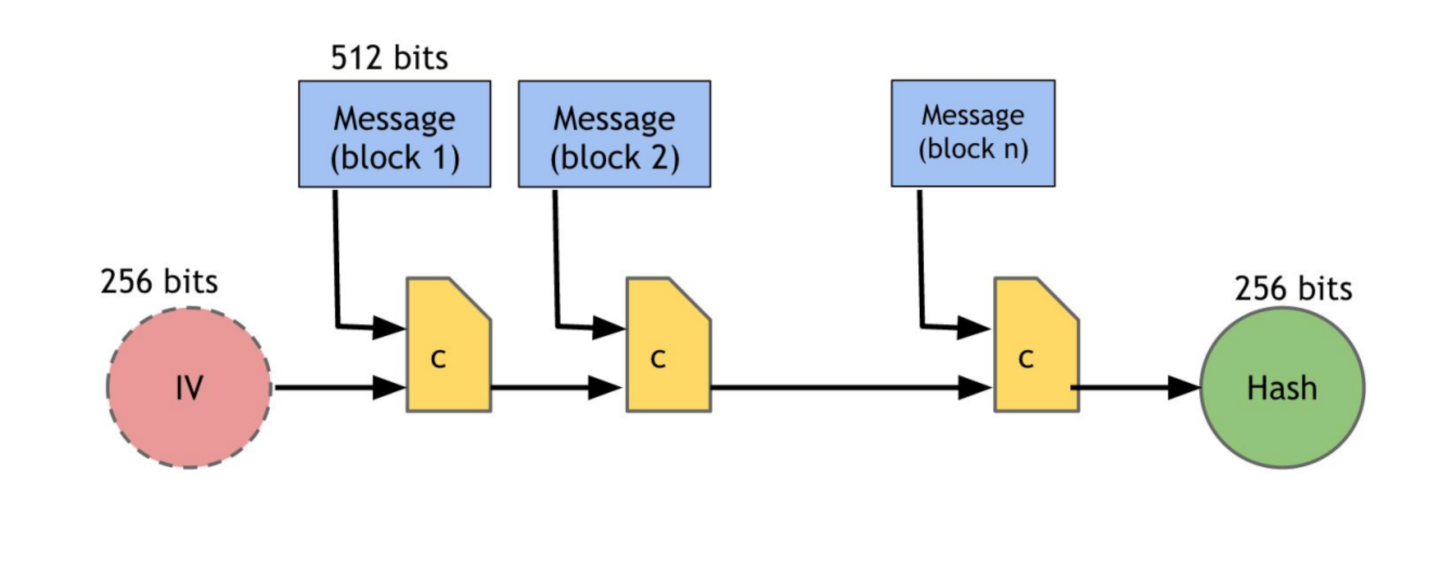
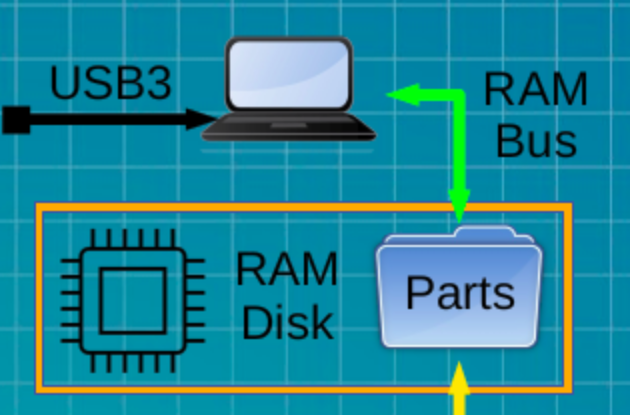
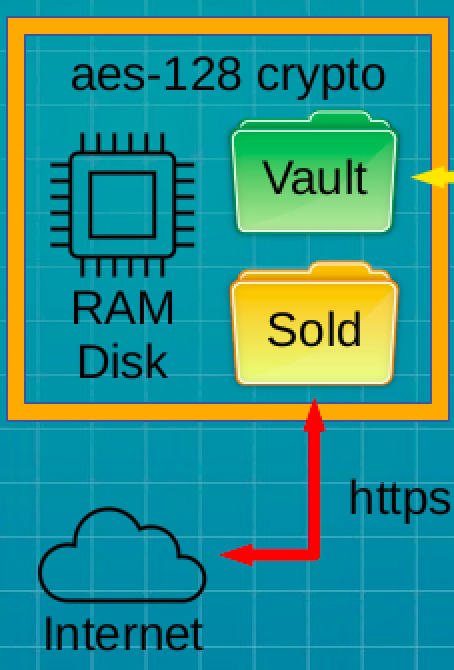
A very clean desktop.
Black wallpaper and dark mode make Oracle Linux 10 presents a clean graphic user interface (GUI) with the Gnome 47 desktop and minimalism of Wayland. Think of a clutter free tablet using a mouse, and you understand the approach.
Look at the left edge of the ribbon atop the screen. The tip of the mouse highlights the bright-bar dim-dot, ready for a click. Right or left will do.
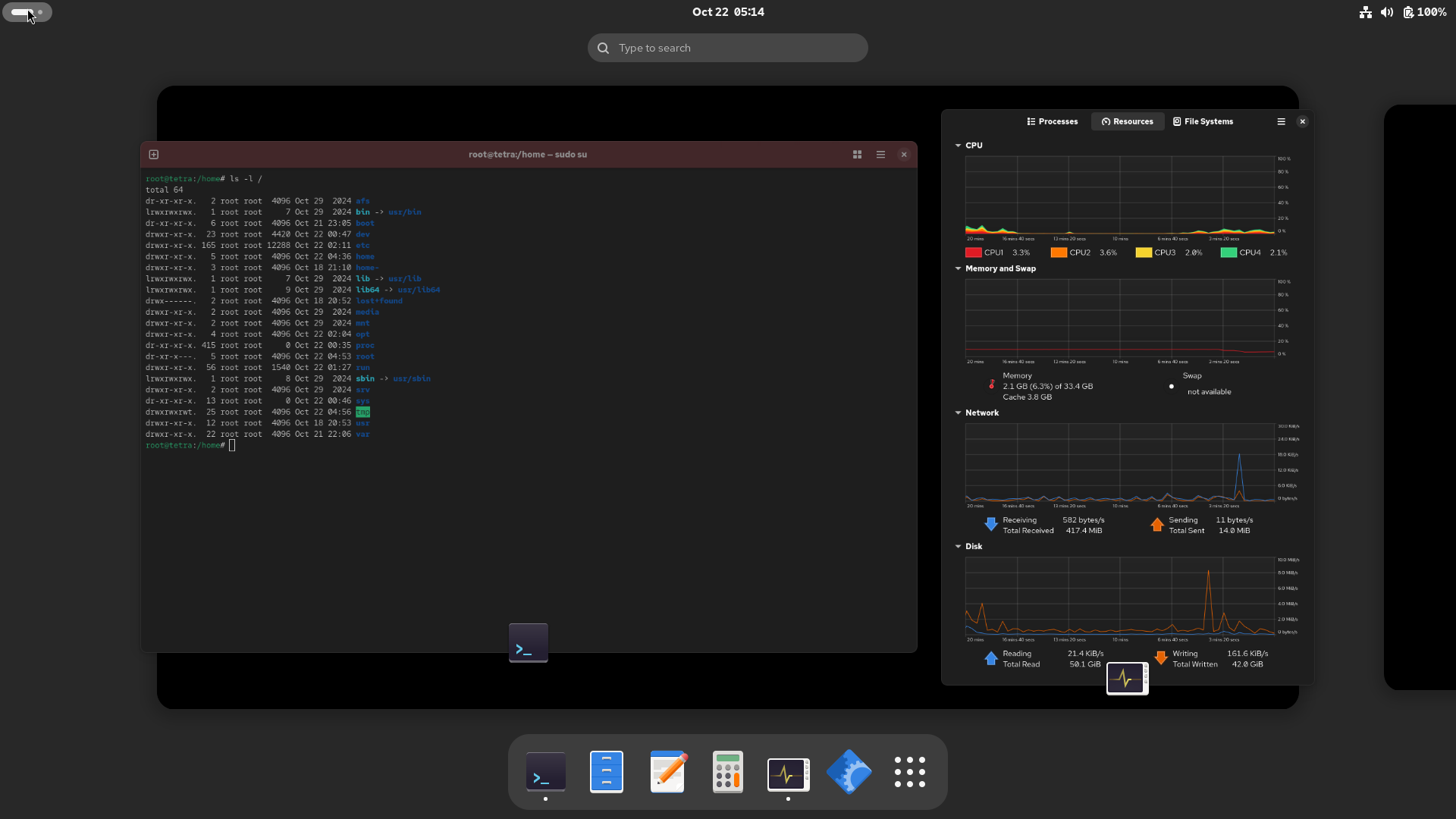
When clicked, the active desktop shrinks. A second desktop, with more if needed, is to the right. Your “Dash” appears at the bottom. I have graphical System Monitor and Terminal windows open. Other minimized windows would dynamically appear in the shrunken workspace. Still clean and free of clutter.
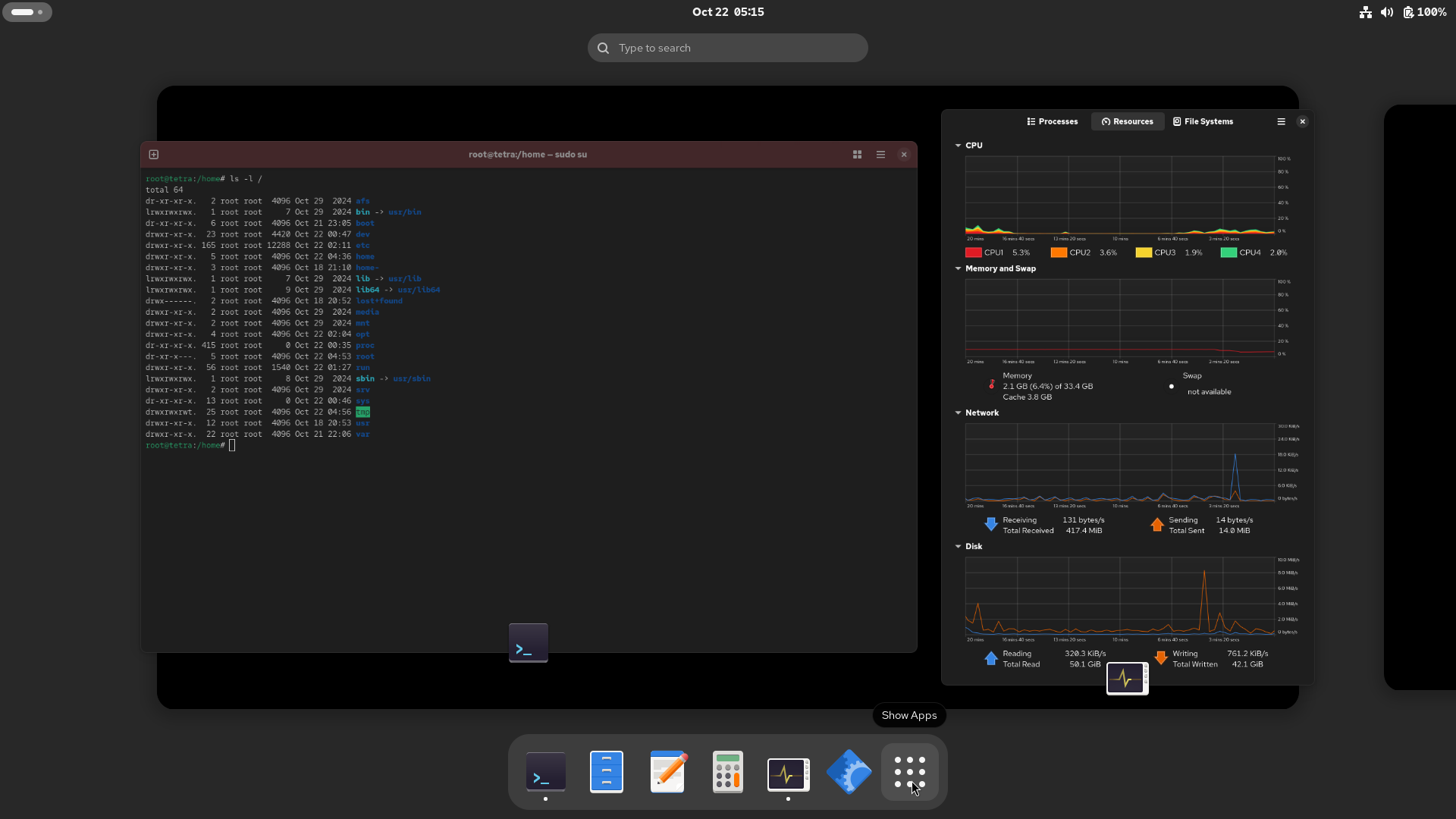
The pointer now illuminates the nine-dot icon in the Dash. This may be familiar to users of Chrome, or other offerings under the Alphabet umbrella. Only a left click will bring up the “installed” apps selection.
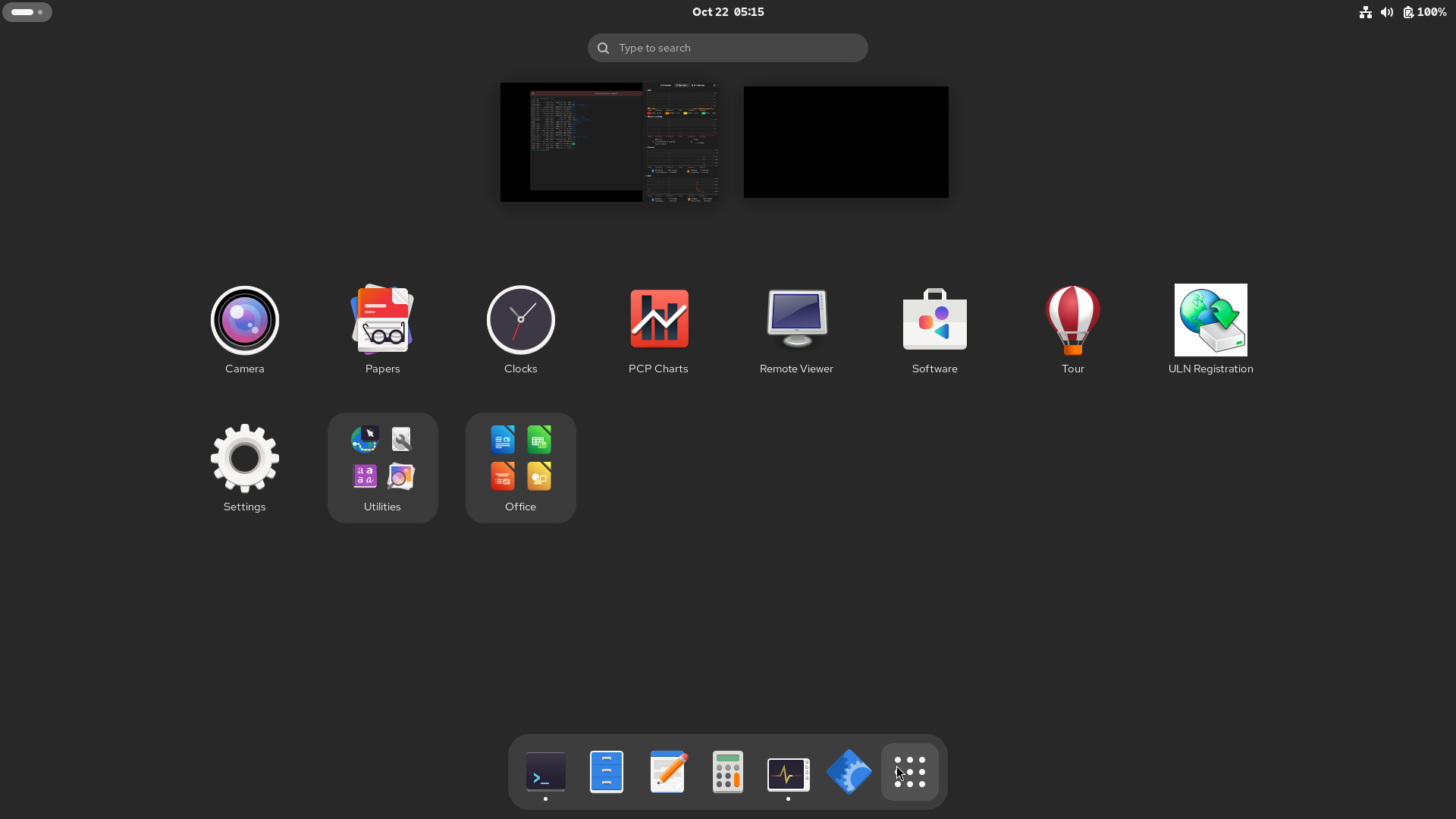
If it’s not pinned to your Dash, it’s on this screen. Utilities was there, out of the box, but Office was created after installing LibreOffice from a tarball, using the dnf localinstall command. By dragging one Office app over another, a group spawned. After dragging all the apps into the group, a double-click opened it.
Dragging an icon in the group, over and left of another, will push the stationary icon to the right, making a spot to drop the dragged icon.
There is surprisingly little to learn when using this GUI. Yes, there are a great many sliders and adjustments under Settings, two ways to get there, and some quick-access controls in the upper-right corner.
In this respect, the ribbon layout matches the mouse. Left to act on and do things, and go right for administration. A healthy and complete exploration of the settings is strongly encouraged. Over the past six years, the settings have not changed, and those presented under Gnome 47 and Oracle Linux 10 (olA) are thoughtful and appreciated. All in all, it’s squeaky clean for an new OS.
Deeper Details
For readers with a thirst for the technical, the rest is yours.
The target system is a Dell with an i5-6300U processor, released 15Q3 and lapsed from Intel’s update list as of 22Q4. With multithreading enabled, trust must rest in reptolines. The quirks in the LCD are annoying, but installing with basic graphics helped. Suspend and resume corrects a fluttering display.
Anaconda, the Red Hat installer, has changed some from the RHEL-7 era. It avoids schizophrenia by restricting the user’s options. While it is possible to open LUKS volumes in the Custom Install dialog, it is not possible to select enclosed file systems or dm devices as installation targets.
An plain-text /boot volume was created in parallel with the preexisting encrypted boot volume on the same auxiliary media as the EFI boot file system. Anaconda agreed to use the ext4 file system in the new boot volume, but insisted on formatting the root volume. The /boot target was not allowed to be encrypted, while the option worked for the temporary root volume.
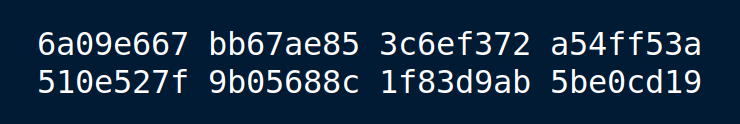
A dark OS upgrade is a security necessity for Ω-systems, as is loading the kernel image and initial ramdisk from encrypted media. Luckily, vgimportdevices brought awareness of the array to the system, proving that olA had the expected behavior having twiddled the appropriate bit in the lvm configuration. Now it was a matter of switching to the proper boot volume.
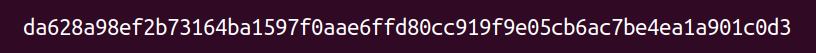
It was necessary no obtain seed files from another system. The seeds contained the automatically generated grub directives to boot from an file system inside a cryptographic container.
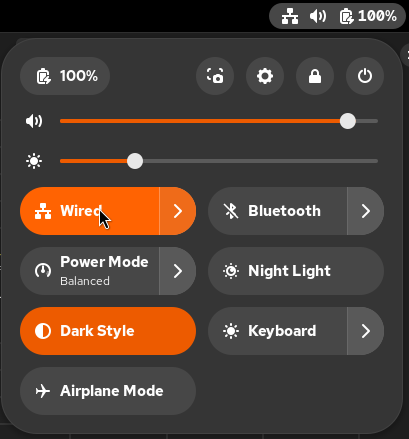
The Admin Panel pops up with a single click in the upper right corner. The pictured pointer toggles the wired network on or off with a second click. This enhances adherence to the minimum connection time mandate of dark updates. This reduces the temporal exposure, of the network attack surface, to the absolute minimum.
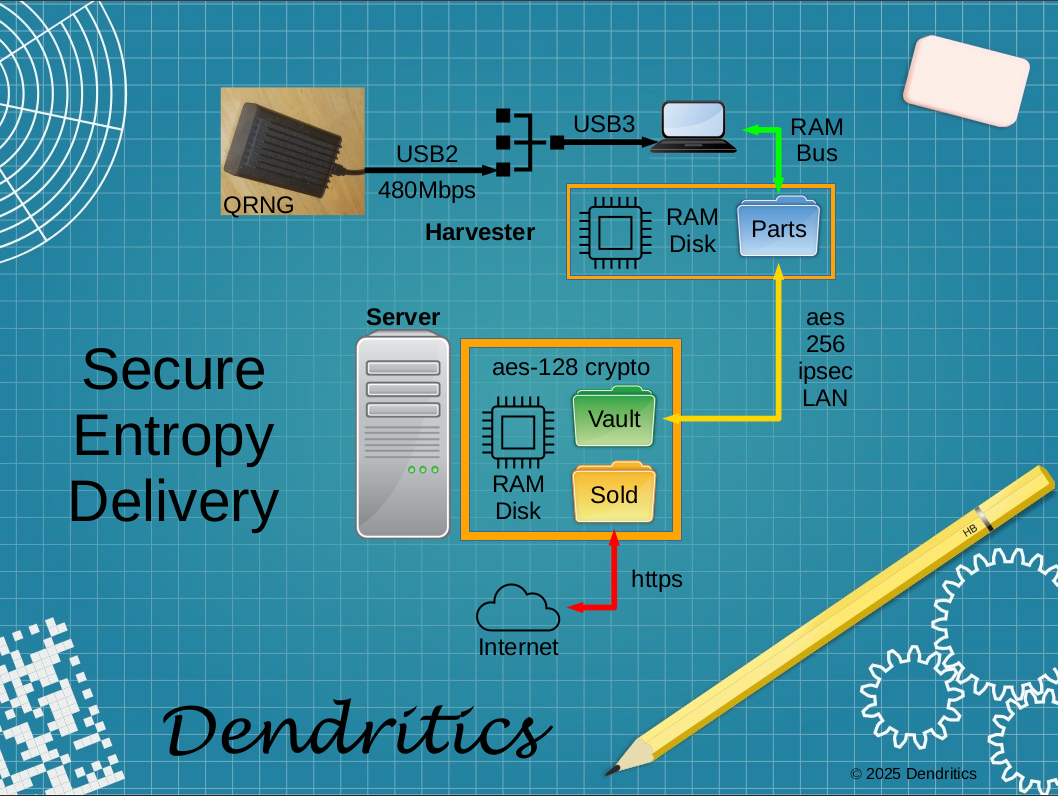
Fresh off the olA success, I packaged my development workstation into tarballs. After duplicating them securely over the network, the release update to 22.04.03 LTS was kicked off. After a cleanup and a restart, it ran like the wind for a strong hour. After resolving a handful of config file updates, and another half hour, it was time for the final restart. The system failed to dismount /run/user/1000 and hung. A ten-second closure of the power-on switch shut down the system.
The restart looked normal, until the root volume was mounted. A missing library was needed to perform LUKS setups. Prior to root being online, modules in grub handled the task. A copy of the library was located next door, but getting it to the target was a bit of a yak shave. The system boots, but glitches to emergency mode. From there, the rest of the system can be unlocked.
Ubuntu Gnome Wayland — Settings ⇒ About
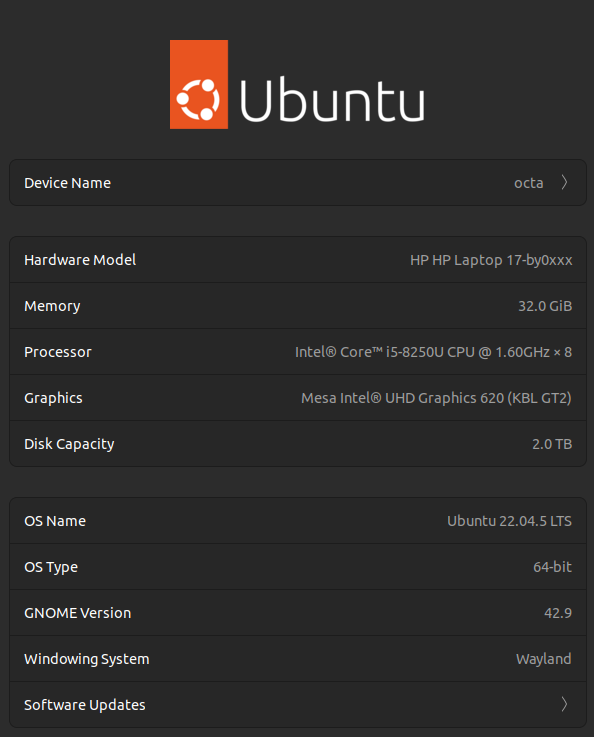
The above is presented as proof of function, as bumpy as it may be. It is presented as a comparison of style. It is a snippet from the action pane in the setup window that takes two clicks to get to. Many system and all desktop settings may be reviewed and possibly modified in the Settings window.
Ω soldiers on