Probability is an enticing headache. The number of possible 64 KiB entropy files is easy to write: 25665,536 We get this from place value in number theory. The Gnome calculator overflows. Would be nice to know how many digits it is in normal human base 10.
Napier gave us the tools. Four centuries hence they still work. Just as log2 of a number gives the effective number of bits (ENoB), while the common log will give us the effective number of decimal digits. Type log(256) into your Gnome calculator then multiply by 65,536.
Rounded up to a whole number. We need 157,827 regular digits to count the number of possible files. That makes a mere 78 digits for a 256-bit number look reasonable. The 20 digits of a 64-bit number look tiny by comparison.
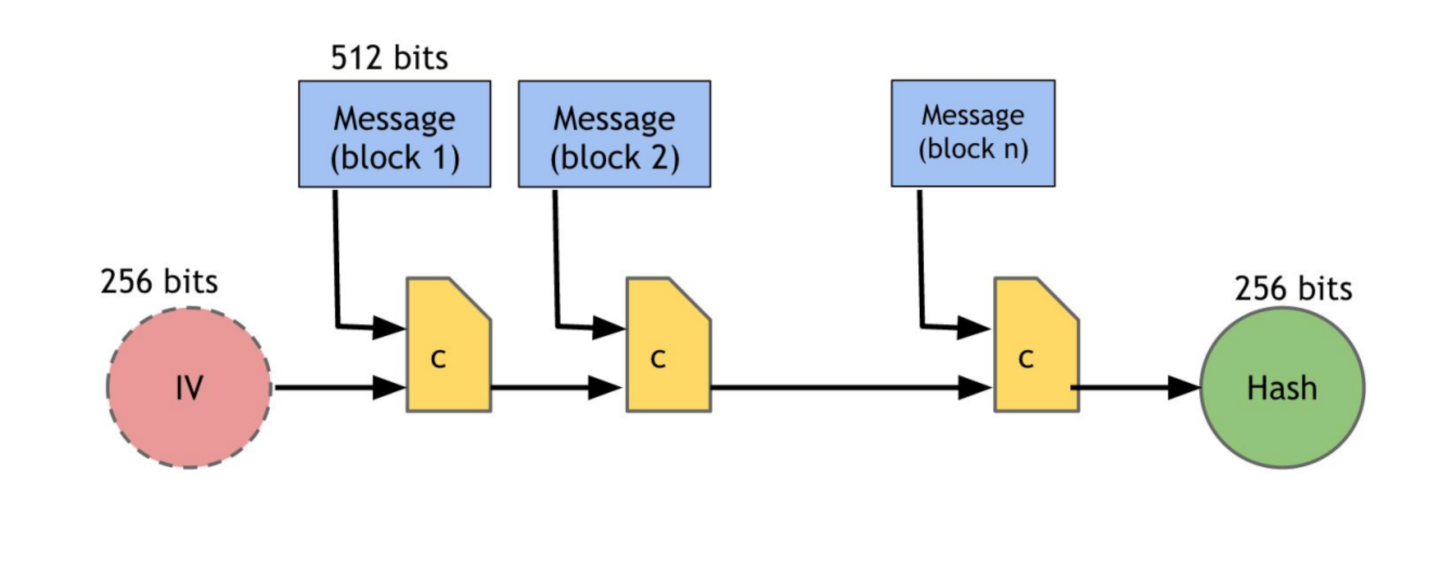
Yes, the above image was acquired from Tony Software and scaled. It’s a partly expanded stream processor, with iterations adding stages. I’d prefer a buffer that gets processed and padded if too short to finish the algorithm — an input tape that needs no rewind. What is fundamental is the initial vector.
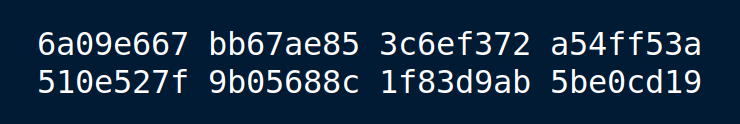
The headache with the algorithm is that the length must be included. An 8-byte big-endian 64-bit integer with the exact number of bits in the message. A running byte count should be maintained. Padding begins with a header marker of a single “1” bit (0x80 in byte parlance) and follows with “0” bits to align the bit-length long-word at the end of a 512-bit block. If the 9-byte suffix won’t fit in the current block (p=0.140625), place the header marker and zero to the end of the block. Remember that the header marker is placed.
If the message filled a larger buffer that was an even multiple of 64 bytes, or the padding of the 56-byte plus block completes the buffer, the buffer must be manually reset. Once space for a final block is targeted, place the header marker if not already placed, or a zero byte otherwise, at the head. Zero the following 55 bytes of the buffer. Auto-increment was made for this.
Convert the message byte count to bits with << 3 and the carve it up or pass the halves through the htonl() function if not already on a big endian CPU. Regardless of any conversion, it can be placed at the buffer pointer. With the suffix complete, finish the computation and output the 256-bit result.
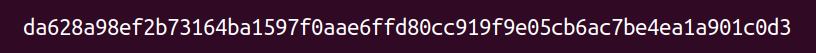
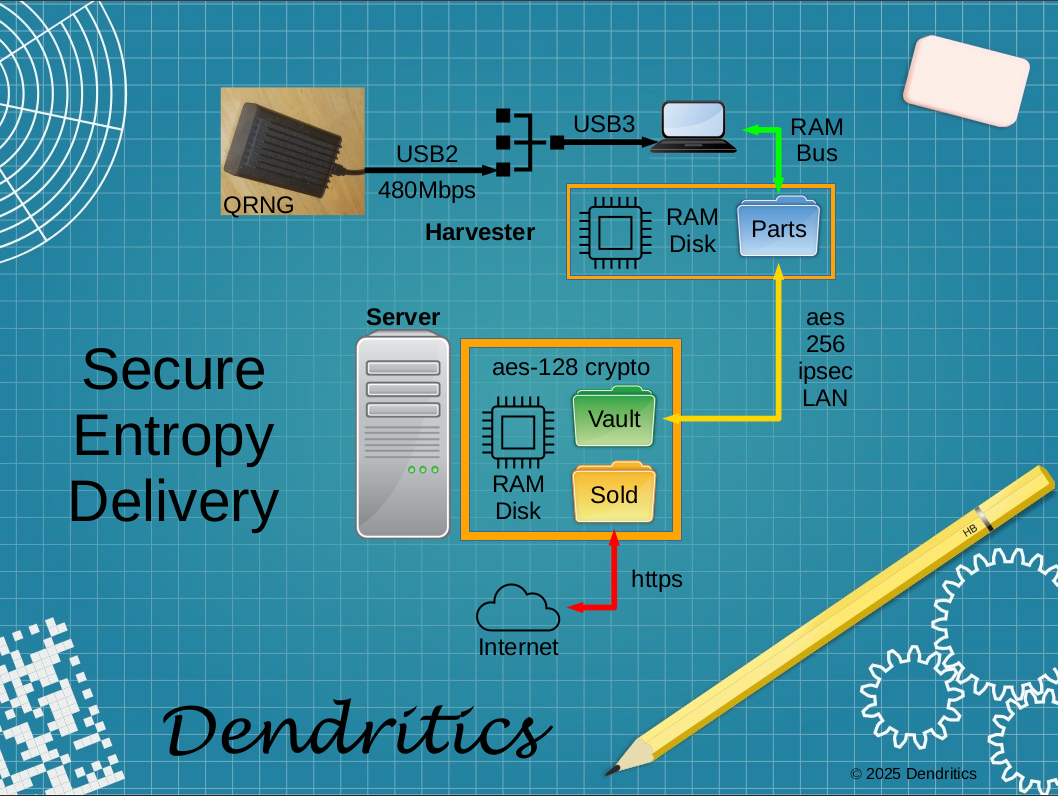
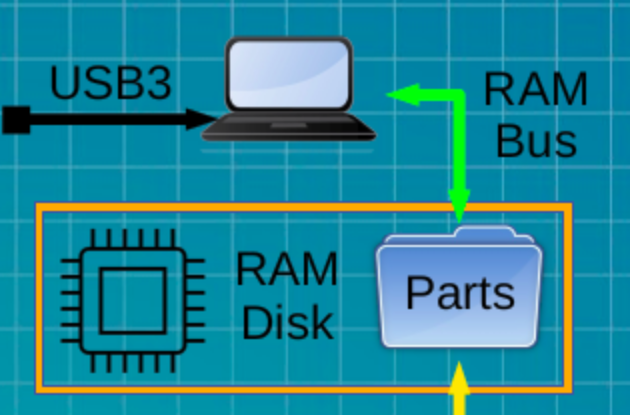
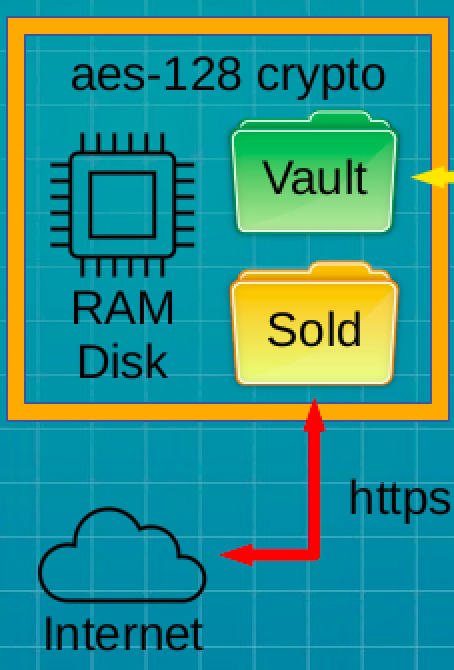
For every entropy file sold via the Dendritics SHQP, a secured database retains the date and time of availability, your order number, and the sha256sum of the purchased file. As an uninterested 3rd party, Dendritics can supply a sworn affidavit of purchase. Downloading any one of our entropy files would mark “ownership” of the media it’s written to, in a legally demonstrable manner.
In the Linux world, it’s quite easy to stuff such a file in a commonly unused portion of media that uses a GPT partition. Caution and due diligence are necessary. With care, the area will survive, even if the drive is re-partitioned and reused. This might be the only way to prove that a stolen, but recovered, hard disk or solid state drive is indeed yours.
In the Mac & Windows worlds, a reasonable strategy is to copy the Entropic Identity file to multiple locations initially. Periodically duplicating the file to newly created folders enhances the possibility of identification, post recovery. While individuals may benefit, organizations have asset management needs that are well served by unique digital media identification.
If ownership verification is on your priority list, drop us an e-mail. Questions may be posted below (click the date). Visit often, as there are some interesting offerings in the works .. perhaps even a Collision Sweepstakes … err … Rebate Offer …